Web application security becomes a major issue, but few courses exist in the school of computer science. An ALTEN web developer had the opportunity to interview Jean-François, Technical Director of ALTEN Canada. He manages the cybersecurity activity for a large investment bank.
As a former software developer, he talks about some basic security fundamentals that you need to know, for your web application development project.
Web applications are the initial target of cyberattacks, representing 53% of the intrusions found on the IS (F5 Labs). However, in the Top 10 computer training programs in the United States, no course on cybersecurity has been identified (Arkasha security).
Jean-François now runs a cyber security center in North America. This center is composed of a “red” team of ethical hackers (pentesters), and a “blue” who identifiy known vulnerabilities. The latter is also coordinating with the development teams to correct these vulnerabilities.
Hello Jean-François, as software developer, I have very few web application security course at school. To begin, do we know all existing vulnerabilities? What are the major categories of vulnerabilities?
We assume that there is nothing unknown as such. Vulnerabilities are detected by the cybersecurity community that lists them. It’s often software editor like Oracle, Microsoft [.etc] which identify and publish them. Do you know how anti-virus software work? We always detect the viruses and then create an anti-virus, so we fight against something we know.
When internal scanners or Pentesters test vulnerabilities or try to penetrate a computer system, they use known techniques and try to exploit known vulnerabilities. The Pentest protocol says that we must test the known faults first . Then, you can look at whether you can pivot into another environment, whether you can get rights, and ask what else you can exploit. At this level, we are no longer going to talk about flaws but about data exfiltration, it is the action following the vulnerabilities exploitation.
For a web developer, it would be interesting to consult the Open Web Application Security Project (OWASP) guides . Open community-powered project, here are some examples of the most common vulnerabilities in web applications :
- Injections (system, SQL, etc.).
- Broken Authentification and Session Management.
- Cross-site scripting (XSS : HTML code injection attack).
- Broken access.
- Security misconfiguration (servers, applications, database or framework).
The pentesters can then use this guide, and say “I will test at least this security breach”. And sometimes, our client request us to perform test for a specific vulnerability.
How useful is OWASP guide to web developer?
The OWASP Project gives the guidelines of web application security. When you read it, there are concrete use cases.
For example, to prevent a SQL injection attack on C# web application, you should not concatenate from end to end, but use such method, such function of the framework. This is important for the learning of a web developer. They need to be trained, and that’s what these open projects are for. In the IT environment, it is a well know project. For those who don’t know it, it’s very important to be aware of it, it increases the developers’ skills.
Are there any development frameworks that could help web developers not to worry about vulnerabilities?
If we take the example of the .NET framework, recent versions offer some basic protections. Let’s imagine that a web developer forgets to process an input through HTTP requests (GET or POST) with a sanitizing procedure. Thanks to the framework, there will be automatic validation on the server side, without the developer having to do it himself manually. This prevents a critical function call (such as an SQL query) performed by hackers.
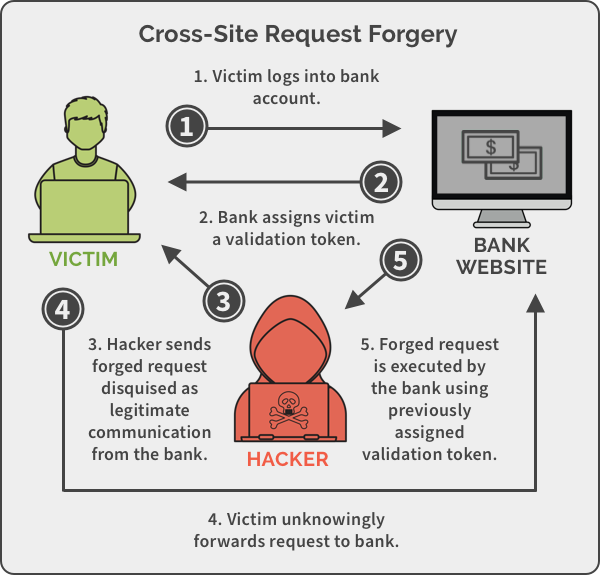
Another example is cross-site request forgery (CSRF) injections , which hijack the trust relationship between a user’s browser and a vulnerable site’s server, to inject a malicious request. The framework also manages this security breach. It automatically generates anti-forgery tokens for HTML web forms input ( source ) to ensure the source of the requests. It is important to know if these queries come from real users and not from a usurped identity.
So yes, the latest versions of the frameworks we use, such as .NET and Java, include basic protections.
But they don’t handle 100% of the cases.
How does your team deals with a framework evolution, like Angular 5 to Angular 6?
The new framework will fix some security breaches. What added value can you bring to web developers?
The main objective is to say: How to secure the code?
Is it by updating the framework that will fix some breaches? Or is it enough to adopt good programming practices for its current framework?
In any case, if it is necessary to change the framework, the right approach is to support the developers to review their code, to make it compatible with the new version.
We regularly organize workshops at our customer’s site to raise awareness among new developers on web application security : what vulnerabilities exist on this framework?
How do we scan for these vulnerabilities? How does the scanner evolve over time? What is our overall approach?
On the other hand, beyond the code, it is important to educate employees or users about good practices in IT security: lock session, prevent phishing campaigns …
The goal is, with our assistance, there will no longer be any vulnerability at the end of the assembly line.
We hear a lot about AI cybersecurity solutions like Darktrace. Is it enough to prevent cyber attacks?
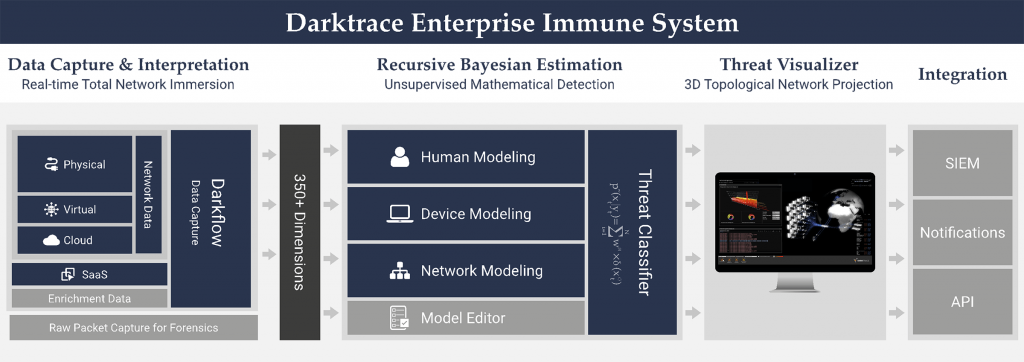
No, Dakrtrace is an artificial intelligent tool. It learns the user’s pattern of life.
Just as anti-virus software detects an anomaly because it knows the behavior of viruses, Darktrace detects an anomaly because it detects user’s suspicious behavior.
The software company showed us whithin two months, Darktrace is able to learn and identify the behavior of a user like:
- The time Jonathan arrives in the morning, the sites he consults, the servers he regulary connects to, his lunch break time, the speed at which Jonathan types on his keyboard, his mouse speed…
if someone connects to his computer, without these patterns, the security system will be immediately notified.
So yes, this tool provides much more durable security. For me, it will be a part of the future.
But regarding the issue of personal data protection (ex : GDPR), the use of Darktrace is limited to a professional context, within a company for example. Such a tool would not be feasible to improve a consumer web application security.
So, how can we proactively detect a vulnerability?
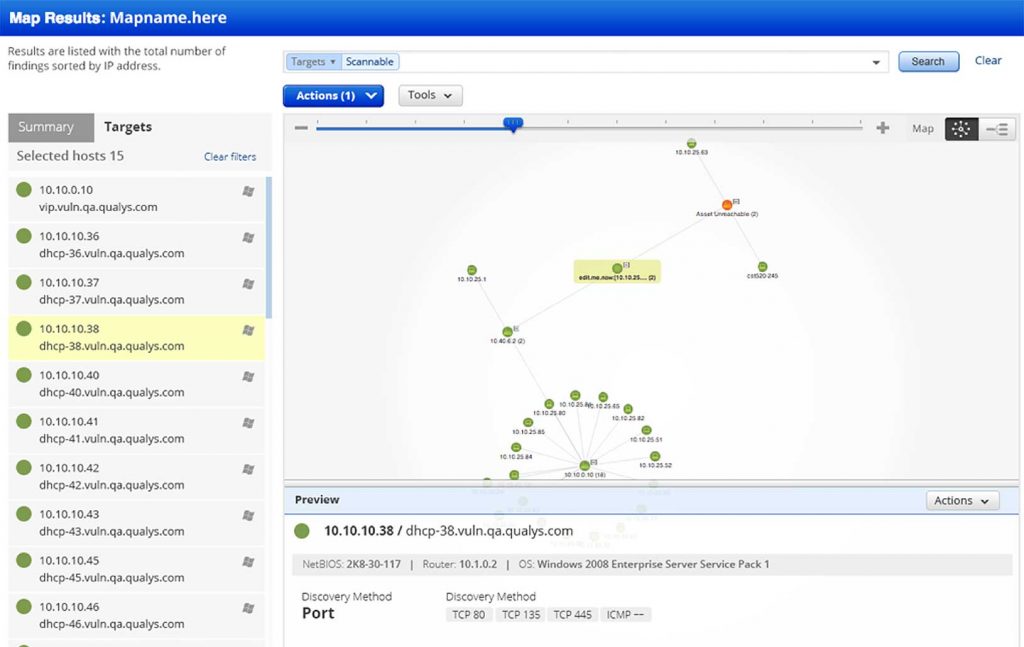
To detect the vulnerabilities, we often think about pentest, but we first use scanners like Qualys, Nessus, Rapid7, Curador…
They go through the networks and detect surface vulnerabilities such as:
- obsolete versions of Windows
- obsolete versions of Open SSL
- the ability to inject JavaScript into a page
- an unsecured website
- no SSL certificate
In the end the scanners will go everywhere, they will scan routers, workstations, computer servers, network switches, IP cameras, smart TVs, IP phones … They will scan all connected equipment.
Once, we had to ask a camera supplier to update their software, because a hacker could have taken control. But in general, modify the configuration is enough to fix the security issue. It does not necessarily require a developer to change the code of its application.
Intrusion tests (pentest), allow analyses and exploitation of vulnerabilities much more in depth than scanners. Agents are installed directly on the computer servers . It’s easier in terms of efficiency and detection. When an agent is installed on a server, it can notify an issue directly to the central system, while a scanner must go through a full network scan to find vulnerabilities.
How can we improve our web application security?
As part of our project, we have .NET and Java developers with IT security backgrounds. They are able to converse with the developers of existing teams to tell them how to write and correct their code.
But how to be more proactive in a context where there are many internal developments?
This is precisely the case with our client : how to avoid vulnerabilities in production when several hundred teams develop software every day… For our client, we participated in the development of a code vulnerability scanner . Before the code goes into production, it goes through an integration tool like Jenkins, then a code scanner like Checkmarx will go through the code.
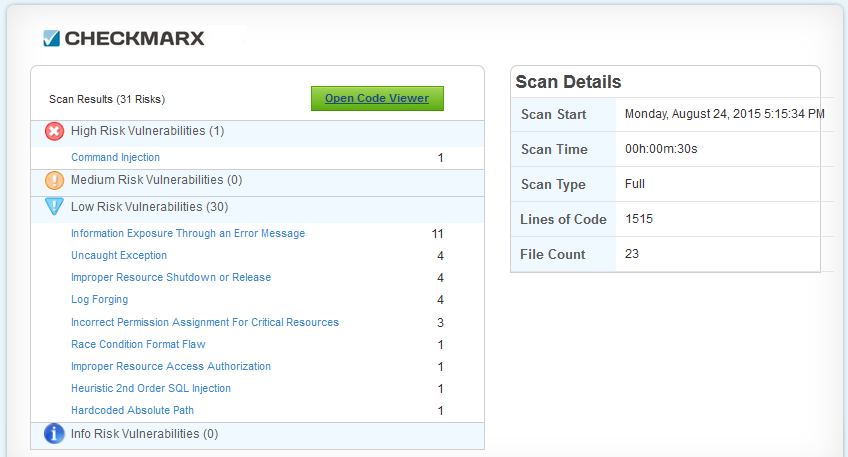
It easily identifies the vulnerabilities we have seen above (OWASP Top 10): SQL injections, XSS (cross-site scripting)… It can even detect the utilization of a vulnerable version of JavaScript library.
> To learn more about the ALTEN cybersecurity project managed by Jean-François:
Red Team vs Blue Team : ALTEN Canada Cybersecurity Center